The Heartbleed bug has been sending netizens panicking for several days now, wondering if their personal information has been compromised during one of their many activities online. You will have noticed your email brimming with status updates from websites you are subscribed to, informing you of either of these things:
- That they are using OpenSSL, and they have taken security measures to ensure your information is not compromised, but as a safety measure you should change your password, or
- That they are using another form of secure server (such as OAuth), and that they are not affected by the said vulnerability, and that your information is safe.
One of the more seriously impacted groups is that of ecommerce, especially since it’s not just their own personal information your ecommerce clients are worried about – it’s their customers’ information as well. Credit card information, online bank accounts, and other data they provide during the buying process may have been put at risk by the said vulnerability in some open-source security software.
The Heartbleed Bug in a Nutshell
The Heartbleed Bug is actually a coding flaw in open-source security development toolkit OpenSSL. Versions 1.0.1 through 1.0.1f were found to have this flaw.
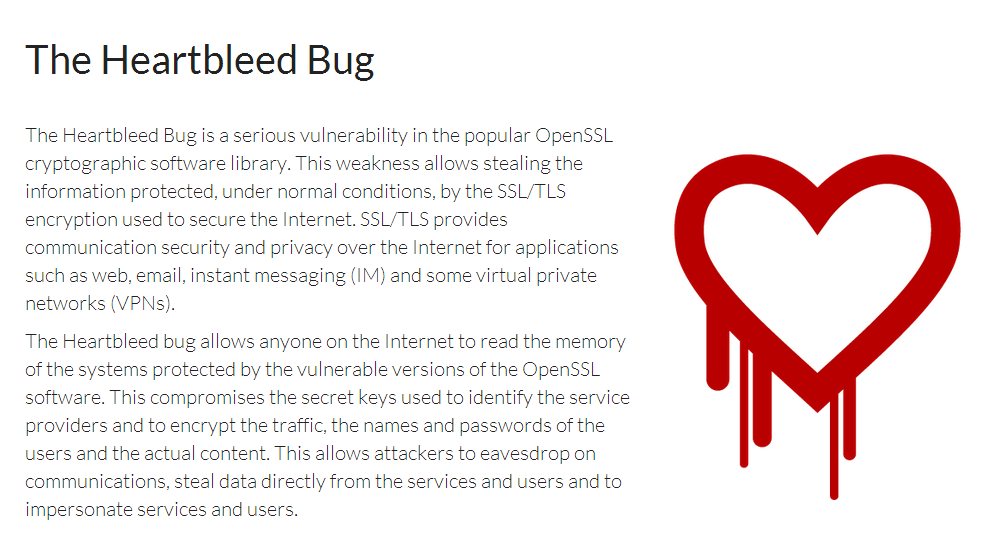
Whenever you complete an activity over a secure server, you send a signal with a specific number of bytes to a secure server, which processes the signal and returns a signal with the same number of bytes. In the aforementioned versions of OpenSSL, though, while users still send signals to the secure server, the server does not send signals back. Hackers can abuse this process because it bleeds information – they can intercept passwords and other private data by exploiting this vulnerability.
An attacker may also request a large chunk of the server’s private memory space in the process. After decryption, this will give them access to long-term server private keys, session keys, and confidential data. The bad thing is that the problem has existed since 2011, but has not been detected until very recently.
Protecting Your Ecommerce Clients
- If you are using OpenSSL, check the version you used for your clients, and inform them immediately if you think their ecommerce sites may be compromised.
- If they are using a version of OpenSSL that is vulnerable to the Heartbleed Bug, switch to an updated version or patch the version your client is using to remove the security threat. You’ll need to revoke and replace security certificates after doing this.
- Have your clients tell their customers to change their passwords after patching the version of OpenSSL used in their ecommerce sites.
- Use a different type of secure server protocol for your future ecommerce sites. We can do this for you when you order a new ecommerce site through our ecommerce web design packages.
- Enable multiple forms of identity verification for online customers, such as phone verification, to ensure security and to avoid false positives.
Talk to your account manager if you have any questions about your ecommerce campaigns, or if you need any assistance with keeping your clients’ sites secure. Sign up now and become our partner to receive your free SEO dashboard and get the tools, services and support you need for your online marketing business. Keep checking back for more updates!